Identity Theft
About Identity Theft
Identity (ID) theft happens when someone steals your personal information to perform unauthorized activities such as fraudulent transactions, whether online or via ATM/POS. These can include stealing credit card information such as the cardholder’s name, credit number, and pin. Threat actors can also carry about identity theft through physical means such as impersonation to commit fraud.
Anyone can become a victim of identity theft, so it is important not to share personal information with unknown or unverified third parties.
How Identity Thieves Use Information:
Identity thieves can use your information in many ways, including:
- Open a new credit card or apply for a loan.
- Open bank accounts and write bad cheques.
- Change your billing address so you no longer receive bills.
Protecting your Online Identity:
You can protect your online identity by adhering to the following basic security practices:
- Create strong passwords that cannot be easily guessed or decoded.
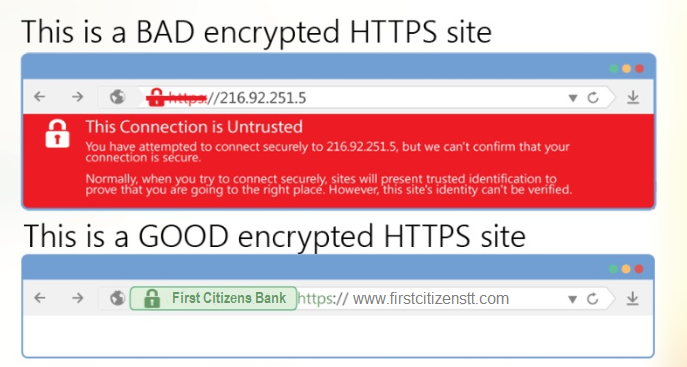
- Before performing a financial transaction online, look for signs that show whether the website is encrypted or not. To do this, look for two things: the trusted security lock symbols and the extra “s” at the end of HTTP in the URL or web address bar: For example
3. Never give personal information to anyone over the phone, over email, or through text message. Many hackers use simple phone calls to learn about you in “vishing.” These bad guys have technology that can display any name and number on your phone when they call (or sometimes text), and they most often pretend to be a representative from a bank. After gaining as much information from you as they need, they can call your bank pretending to be you and commit fraud using your account.
4) Review your bank account statements regularly. Compare receipts with account statements to identify unauthorized transactions.
5) Shred receipts, account statements, and expired credit cards. Doing so can prevent “dumpster divers” (someone who go through your trash to obtain valuable information) from getting your personal information.
Keep Your Smartphone Secure
Identity theft and fraud can strike through any consumer-ready digital device, and smartphones are no exception. Once a fraudster has access to your personal information, they could impersonate you for many reasons, including gaining access to various services, from your bank accounts to your credit card information. This could result in financial loss or other troubles such as financial debt. Therefore, you can protect your smart devices by following these simple tips:
- Check regularly that all your software and applications are updated
Software developers regularly include updates that provide program improvements and bug fixes. Ensuring that these are up to date means having the latest protective measures installed on those programs.
- Make sure that you download applications from reputable companies
Exercise caution when downloading free versions of well-known apps or alternatives that seem similar to apps by established companies. These may appear free, but it is a ploy to collect and use your personal information without your consent.
- Keep copies of essential files
Regularly back up sensitive information stored on your smartphone in a secure and trusted location. - Use secure connections
Avoid logging in to your online bank account or checking your email using public Wi-Fi. These communication channels might not be secure as they are prone to interception by cybercriminals. Also, make sure that any Bluetooth options are turned off if you don’t have to use them.